With Corvee Software, you can rest easy knowing your documents are secure. We built our system to be encrypted from end-to-end, which means the information between your firm and your clients is locked and safe.
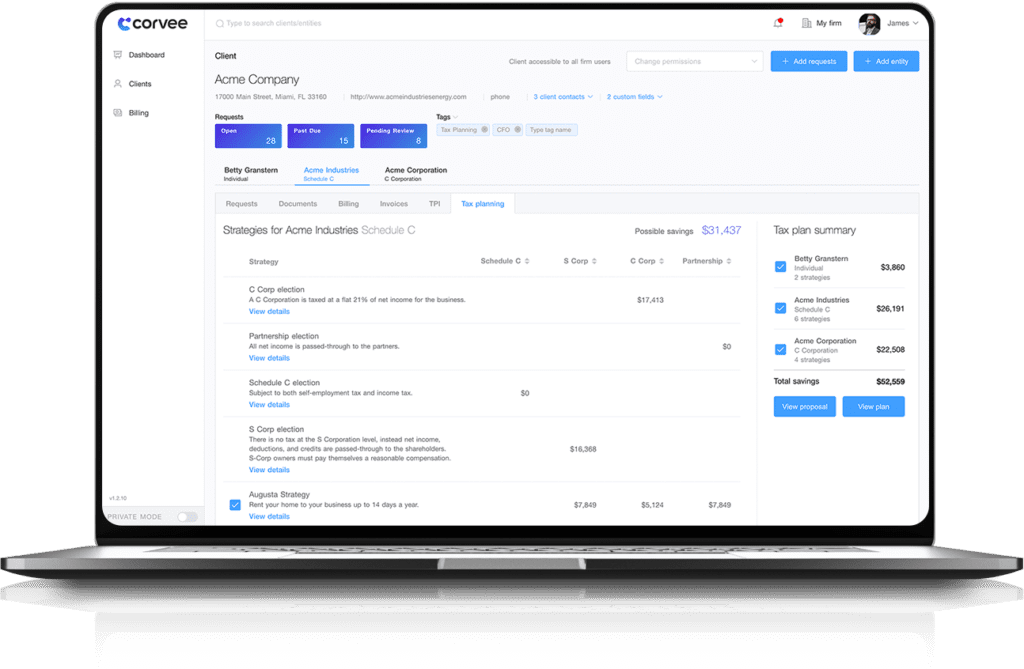
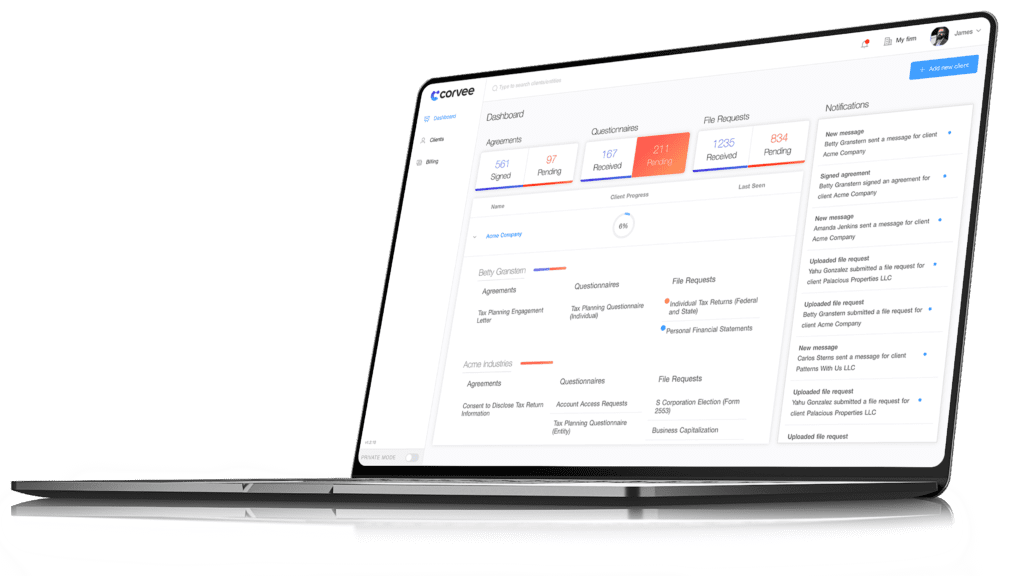
Corvee provides accounting and tax firms the ability to prepare tax plans and proposals, send and receive documents with clients and collect payments all within a highly secure software platform, without the risk of compromising sensitive data.
With most software applications, you rely on the software provider’s ability to keep your encryption key secure. This is security by policy. In contrast, we use security by design which puts you in control of your key using asymmetric encryption.
Many software programs are doing encryption. The difference with Corvee is that we let the user do the encryption with their key instead of us doing it with ours. This means not even Corvee has access to your sensitive client data.

Your data is not just protected by a simple login form. With your encryption key derived from your master password, all your data in our system is invisible to Corvee or any other third party.
This helps to ensure would-be intruders cannot access anything inside our software except you and those you’ve decided to give access to.
Attacks by eavesdropping on information are rendered useless thanks to the Secure Remote Password protocol we implemented, which uses encryption in transit to protect against anyone having enough information to gain access to any information transferred between you, your client or Corvee servers.
We’ve documented the details in our Security White Paper.

Please fill out the form below.
Fill out the form below, and we’ll be in touch.
Please fill out the form below.
Please fill out the form below.
Please fill out the form below.